“Your Package Has a Problem”: Inside the Delivery Smishing Scams Flooding Your Phone
The anticipation of an online order is a familiar feeling for millions of shoppers. The process is marked by…
!["Your Package Has a Problem": Inside the Delivery Smishing Scams Flooding Your Phone 1 A person's hand holding a white smartphone, which displays a fraudulent text message impersonating USPS. The message reads 'USPS: Your package has an unpaid shipping fee of $.85. Please update your details here to avoid delays: [Malicious-Link.delivery-update.net]'. In the background, out of focus, are stacked cardboard delivery boxes, a laptop, and a credit card, emphasizing the context of online shopping and potential fraud.](https://www.fraudswatch.com/wp-content/uploads/2025/10/Smartphone-Displaying-a-USPS-Smishing-Scam-Text-768x768.png)
The anticipation of an online order is a familiar feeling for millions of shoppers. The process is marked by…

I. Introduction: An Inside Job Shakes the Telecom Sector In a stark illustration of the vulnerabilities lurking within major…

The digital age has brought unprecedented connectivity and convenience, but it has also opened the door to a new…

The Digital Age Dilemma: Convenience vs. Catastrophic Risk The digital revolution has woven itself into the fabric of our…

WASHINGTON, D.C. – In a sweeping international operation, the U.S. Justice Department has unsealed charges against two Russian nationals…
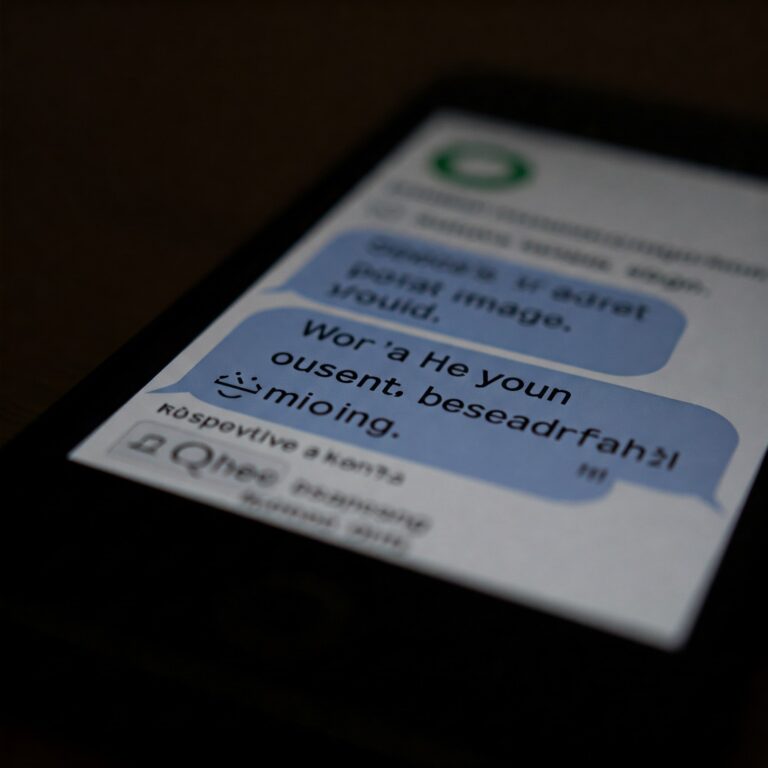
The Federal Bureau of Investigation (FBI) has issued a stark warning to millions of iPhone and Android users across…
The high-stakes world of artificial intelligence (AI) development has become a battleground for global technological dominance. A new superseding…

The digital age, while offering unprecedented opportunities for connectivity and innovation, has also spawned a dark underbelly of cybercrime….

The year is 2025. While digital payment technology has made leaps and bounds in convenience and security, credit and…

Despite the rise of digital payments, checks remain a common method of transaction in 2025. This continued reliance makes…

Who is CDK Global? CDK Global is a leading provider of integrated data and technology solutions for the automotive…