The Trust Illusion: Your Definitive Guide to Surviving the Top AI Scams of 2025
The $25 Million Video Call and the New Reality of Fraud In early 2025, a finance clerk at a…
Empower your business against fraud with Fraudswatch’s cutting-edge fraud prevention solutions. Detect and stop fraud attempts in real-time, protect your revenue, and build customer trust. Explore advanced tools and strategies to stay ahead of fraudsters.

The $25 Million Video Call and the New Reality of Fraud In early 2025, a finance clerk at a…
!["Your Package Has a Problem": Inside the Delivery Smishing Scams Flooding Your Phone 2 A person's hand holding a white smartphone, which displays a fraudulent text message impersonating USPS. The message reads 'USPS: Your package has an unpaid shipping fee of $.85. Please update your details here to avoid delays: [Malicious-Link.delivery-update.net]'. In the background, out of focus, are stacked cardboard delivery boxes, a laptop, and a credit card, emphasizing the context of online shopping and potential fraud.](https://www.fraudswatch.com/wp-content/uploads/2025/10/Smartphone-Displaying-a-USPS-Smishing-Scam-Text-768x768.png)
The anticipation of an online order is a familiar feeling for millions of shoppers. The process is marked by…
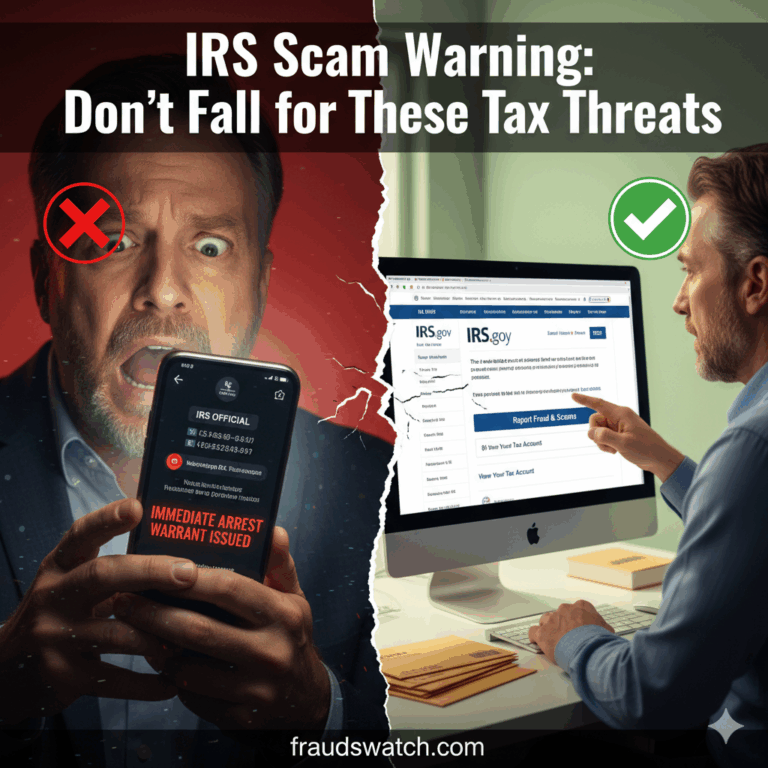
The Call That Steals More Than Money The phone rings on a Tuesday afternoon. For Brad, a new father…

In our hyper-connected world, your personal information is one of your most valuable assets. Unfortunately, it’s also a prime…

The Crypto Crime Epidemic: A Five-Year Financial Analysis The proliferation of digital assets has been accompanied by a parallel…

Unearthing a Persistent Threat In an era dominated by sophisticated cyberattacks and complex digital fraud schemes, it might seem…

Introduction: The Pervasive Threat of Malicious Software In today’s interconnected world, digital technologies underpin nearly every aspect of modern…

The sudden, sinking feeling of a hand patting an empty pocket or rummaging through a purse only to find…
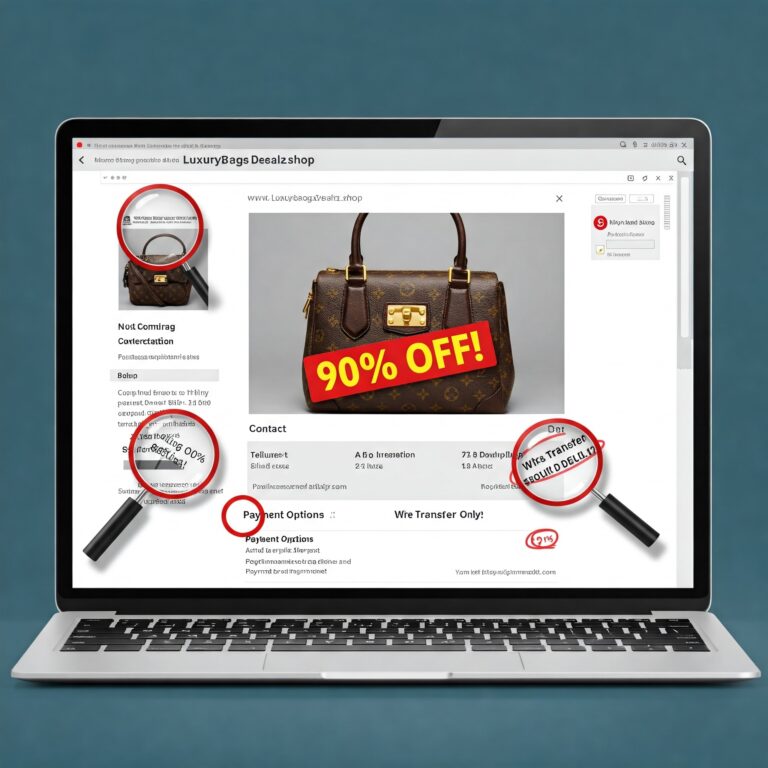
(Date: April 8, 2025) The digital marketplace is a marvel of modern convenience. With a few clicks, consumers can…

The internet connects us, empowers us, and entertains us. It’s an indispensable tool for modern life. But lurking beneath…

Protect Your Privacy and Business: Latest Tips, Essential Strategies, and Answers to Key Questions About Information Theft from Trash…

The digital age has brought unparalleled convenience to banking and payments, but it’s also opened the door to sophisticated…

The intentional misrepresentation of information or identity to deceive others for financial gain stands as a pervasive and ever-evolving…

The digital age has brought unprecedented connectivity and convenience, but it has also opened the door to a new…
The allure of a dream home or a lucrative investment property can be powerful. However, the rise of artificial…

The financial services industry is under siege. In an era defined by rapid digital transformation, financial institution groups –…

Learn how to identify and avoid cryptocurrency scams in 2025. This comprehensive guide covers the latest scam types, red…

The digital age has amplified both the connectivity and the vulnerability of our communities. Investment scams, particularly affinity fraud,…

The Digital Age Dilemma: Convenience vs. Catastrophic Risk The digital revolution has woven itself into the fabric of our…

In an era defined by rapid technological advancement and increasingly sophisticated methods of deception, the battle against fraud and…