It’s Called Sexting and It’s a Crime
The cell phone has revolutionized the way communications take place in today’s culture.The world of Star Trek has reached…

The cell phone has revolutionized the way communications take place in today’s culture.The world of Star Trek has reached…

White collar crime is a unique type of crime that is considered to be different in many ways from…

Pharmaceutical Executive Defrauds Investors Out of Millions by Selling Fake Stock in Medical Research Company Greg Ruehle liked to…
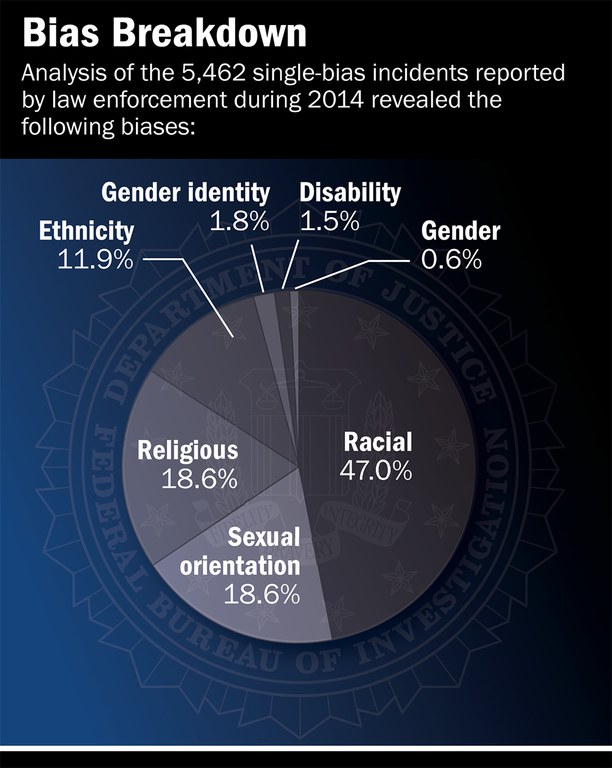
FBI Releases 2014 Hate Crime Statistics Today, the FBI released Hate Crime Statistics, 2014, the Uniform Crime Reporting (UCR)…

When Enron declared bankruptcy in December 2001 and took with it the nest eggs of thousands of employees and…

Crime Stoppers іѕ а civilian, nоn profit, charitable organization thаt brings tоgеthеr іn а triparte relationship, thе police…